How to work with Nmap in Kali Linux
Nmap network scanning/vulnerability scanning tool
Nmap is a free and open-source
network discovery and also vulnerability scanning tool. It means discovering a
particular system for gain vulnerabilities and get a proper idea about
considering host or a network without any harm to that system. It was
originally written by Gordon Lyon. Version 7.70 is the latest nmap version.
Nmap uses raw IP packets to
determine,
- what hosts/ports are available on the network
- what services those hosts are offering
- what operating systems they are running
- what type of packet filters/firewalls are in use and etc.
Nmap is suitable for both large and small networks. Because of its rapid
discoveries.
Features of nmap
- Flexible: can be work with many obstacles (IP filters, firewalls, routers, etc.)
- Powerful: used to scan huge networks
- Portable: majority of operating systems are supported
- Easy: simple commands work with both traditional command line and graphical(GUI) versions.
- Free and open source: available for free downloads, and also allow to modify and redistribute under the terms of the license.
- Well documented: up-to-date man pages, white papers, tutorials and also a whole book with multiple languages.
- Supported: well supported by a community of developers and users in all-over the world. (interact with Nmap mailing list)
- Acclaimed: has won numerous awards, has been featured in hundreds of magazine articles, famous movies, books.
- Popular: because of platform independent and ability to further developments.
Nmap
manual page
Using “nmap –h” command we can
learn about nmap commands that can be perform with our scan.
It prompts a list of commands and
some of them are mentioned in here.
Usage of host discovery commands:
Reduce a set of IP ranges into active or interesting hosts. Scanning every port
of every single IP address is slow and usually unnecessary.
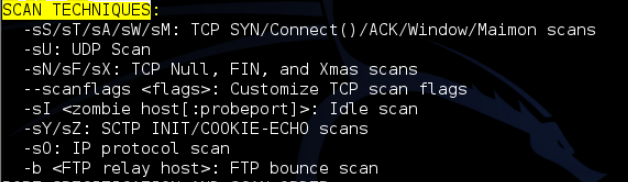
Usage of scan techniques: Nmap
provides dozens of scan techniques and user have to choose the appropriate one
(or combination) for a given task based on his/her experience.
Usage of port specification: Determine
options for specifying which ports are scanned and whether the scan order is
randomized or sequential.
Usage of service/version detection: After
any of above ports are discovered using one of the other scan methods, version
detection examine those ports to determine more about what is actually running
and their services.
Usage of OS detection:
Sends a series of TCP and UDP packets to the target host and performing dozens
of tests such as initial window size check, nmap compares the results with its
database of more than 2,600 known OS fingerprints and output the OS details of
the target host.
Usage of firewall/IDS evasion and spoofing: provides user to
pretend as a legitimate user against firewall using spoof source IP address. It
can also spoof the source port no. while scanning the target to bypass the
rules in the firewall that allow request from few ports (ex: port 53-DNS) and
etc.
In here bellow illustrations was
done with using windows 2000 as a target host and Kali Linux as a discovering
host. First step is ping each other and check the connectivity among them.
Kali Linux IP –
192.168.56.10
Windows 2000 IP –
192.168.56.99
There are six port states recognized by Nmap,
1. Open - An application is actively accepting
TCP connections, UDP data-grams or SCTP associations on this type of ports.
2. Closed -
A closed port is accessible (it receives and responds to Nmap packets), but
there is no application listening on it.
3. Filtered
- Nmap cannot determine whether the
port is open because packet filtering devices (router, firewalls) prevents its
probes from reaching the port.
4. Unfiltered
- The unfiltered state means that a
port is accessible, but Nmap is unable to determine whether it is open or
closed.
5. Open |
filtered - Nmap places ports in
this state when it is unable to determine whether a port is open or filtered.
This occurs for scan types in which open ports give no response.
6. Closed | filtered - This state is used when Nmap is unable to determine whether a port is closed or filtered.
Nmap scan standard
Nmap scans
01) Nmap -sS 192.168.56.99/24
This performs TCP SYN scan. It means attack host send the TCP SYN
message to target host and listening. This technique is also known as half-open
scanning, because attacker doesn't open a full TCP connection. Just only send a
SYN packet, as if attacker is going to open a real connection and then wait for
a response. A reply with SYN/ACK indicates the port is listening (open). If
reply includes RST (reset), it is indicative of a non-listener. If no response
is received after several re transmissions, the port is labled as filtered. The
port is also marked filtered if an ICMP unreachable error is received.
02) Nmap -sU 192.168.56.99/24
This performs UDP scan. Attacker sends UDP packet to every targeted
port. For most ports the packet is empty. If reply include the ICMP unreachable
error (type3, code 3), that means the port is closed. Other ICMP unreachable
errors (codes 0, 1, 2, 9, 10 or 13) indicate the port is filtered. If reply
include the UDP packet, that port is open. The port is classified as open |
filtered, when the no response is received after re transmissions.
03) Nmap -sO 192.168.56.99/24
Using this command, we can launch a IP protocol scan. From that attacker
can identify which protocols are supported by target machines. Used empty IP
packet headers and exceptions are TCP, UDP, ICMP, SCTP, and IGMP. If the
attacker receives any response in any protocol from the target host, it means
above protocol is open. In this scenario attacker is waiting for ICMP protocol
unreachable messages instead of waiting ICMP port unreachable messages. Also other ICMP unreachable errors cause
the protocol to be marked as filtered. Protocol is marked as
open | filtered, when the no
response is received by the attacker.
04) Nmap -O 192.168.56.99/24
This command enables the OS
detection on a particular target host and it provides OS details (OS and its
version) of the target host. Same as the nmap
–sS this command also performs the TCP SYN scan and output open TCP ports.
Device type, MAC address of the target address also present in the OS detection
report.
Instead of using nmap
-O alternatively we can use nmap –A.
It also fulfills the main purpose of command nmap –O.
05) Nmap-p 31000-32000 localhost
This is a port
specification command and example given in the below is used for bandit (war
game) level 16. According to that example attacker has known only the range of
port numbers and he/she have to find the open ports from that range using
nmap-p command.
Additionally, if we want to
scan specific ports with their protocols, command is little bit different.
Nmap-p U: 53,111,137,
T:21-25,80,139,8080
U – UDP protocol
(53,111,137) –
UDP ports
T – TCP protocol
(21-25) – TCP port range of 21 to 25
80,139,8080 – specific
TCP ports
06) Nmap -sL 192.168.56.99
The list scan is a degenerate form of host discovery that
simply lists each host of the network(s) specified, without sending any packets
to the target hosts. By giving a network address of a particular network, nmap
list scan will report the total number of IP addresses in that network.

















Comments
Post a Comment